Starting a business is an exciting time – you're finally taking on your own business and want everything to work from day one. But before you can start serving clients, you need a solid technical foundation. IT is not just computers and the Internet, but a whole set of elements that must work together: hardware, network, software, security, licensing, and even regulatory compliance.
This guide was created to simply and practically guide you through the most important decisions you'll need to make in your first few weeks of business. You won't find complicated language or complicated definitions here—instead, you'll get a specific checklist of steps and examples from various industries.
You will learn, among other things:
• what computers, routers and printers are best for a small business,
• why a domain and business email are your first mandatory investments,
• what to invest in first so as not to burn through the budget,
• how licenses work (and what happens if you don't buy them),
• what is backup 3-2-1 and how to protect your company's data,
• how to prepare for legal requirements – from GDPR to KSeF,
• what IT solutions are key in various industries (from transport to accounting offices).
The article is divided into thematic sections, each answering one of the most frequently asked questions by new entrepreneurs. You can read the entire article step by step or skip ahead to the sections that are most relevant to you.
The goal is simple: after reading this, you will know what you need to have from the first day of your company's operation, what you can implement later, and what it is better to give up so as not to expose yourself to unnecessary costs or risks.

30-day plan – a simple action plan
You can complete the plan below sequentially or in parallel. Each block includes specific steps, an end result, a brief explanation of why you're doing it, and how to verify it's working. The language remains simple, with technical terms explained in parentheses.
Day 1-3: Domain, Business Email, Accounts, and MFA
Objective: organized online company identity, consistent email addresses, secure login.
Steps to follow:
Register a domain (e.g. yourcompany.pl). Choose a short name, without hyphens.
Create a master mailbox (e.g. biuro@twojafirma.pl) and owner's account (Your name and surname).
Configure mail DNS: records SPF, DKIM, DMARC (these are "business cards" for email servers that confirm that your emails are real).
Choose a plan Microsoft 365 for Business (Basic/Standard/Premium) and create user accounts.
Enable MFA (two-factor login) for everyone: phone app or hardware key.
Enter password manager and short password policy (min. 12 characters, unique, change only after incident).
Set up aliases and shared mailboxes (e.g. sale@, contact@) instead of "anonymous" accounts.
Prepare the offboarding procedure (list: revoking access, transferring files, deactivating account).
Final result:
• Email addresses in the company domain, working SPF/DKIM/DMARC, accounts with MFA, "Password Policy (version 1.0)" document.
How to check if it works:
• Test sending email to an external address → does not go to spam.
• M365 dashboard shows 100% users with MFA.
• You log in to the portal and Outlook on two devices without errors.
• The offboarding procedure fits on 1 page and is understandable to a non-technical person.
Two traps to avoid:
• Buying a domain "for a private person" instead of for a company.
• Lack DMARC – increases the risk of your brand being impersonated.

Day 4-10: Hardware and network (router, Wi-Fi, printing)
Objective: stable internet, decent Wi-Fi, properly selected computers and printers – without overpaying.
Steps to follow:
Role inventory (e.g. accounting, sales, production) → assign to each role hardware profile: "light office" (Word/Excel/Teams) or "heavy office" (large files, CAD).
Purchase of laptops with at least 16 GB RAM (often enough for "light" systems), NVMe SSD drive and NBD/on-site guarantee.
Disk encryption (BitLocker) and Asset Tag sticker (easy hardware identification).
Router for the company with the possibility VLAN (separation of guest and IoT devices) and backup LTE/5G.
Wi-Fi Project: separate SSID (network) for guests and employees, coverage test in each room.
Printers/Scanners: scan to e-mail/SharePoint function, PIN code protection for printouts, count TCO (toner/service cost).
Docking and monitors: one docking station + two 24″/27″ monitors for office workstations.
Network Map Document: admin passwords in the password vault, saved VLAN/SSID settings, router access.
Final result:
• Stable connection, Wi-Fi without "holes", computers compatible with roles, a set for comfortable work, ready "Network Map".
How to check if it works:
• Speedtest and ping in 2-3 places in the office, no video call drops.
• The guest only sees the internet, not printers or file shares.
• Scan to email/SharePoint works from both printers.
• Equipment can be found by its Asset Tag in the inventory.
Two traps to avoid:
• One "home" router for everyone – no network segmentation.
• Selecting a printer solely based on the device price (ignoring TCO).
We can design the network and Wi-Fi and select the hardware so that it operates stably from day one – with short post-implementation documentation.

Day 11-20: Licenses and Safety Basics
Objective: legal software, clear set of licenses and real IT security in the company.
Steps to follow:
Choosing an M365 plan: Basic/Standard/Premium – save who and why has a given plan (e.g. management: Premium).
Enabling endpoint protection (EDR, e.g. Microsoft Defender for Business) on all computers.
Device management in Intune: update policies, blocking the installation of unauthorized applications, standard set of programs.
Legality audit: write down licenses (system, Office, industry programs), keep invoices/numbers.
File access rules: "departmental" groups, shared directories, minimum permissions.
Macro lock from unsigned sources and basic rules in email (e.g. warning against shortened links).
Short anti-phishing training: how to recognize suspicious messages, how to report an incident.
Incident Response Plan (1 page): who to notify, how to disconnect equipment, how to change passwords.
Final result:
• Clear license matrix, active EDR and Intune policies, basic security procedures, evidence of software legality.
How to check if it works:
• Intune report shows 100% devices in policies.
• EDR detects a test EICAR file (control, harmless).
• A user without permissions will not be able to install the program on their own.
• Employees know how to report a suspicious email.
Two traps to avoid:
• “We have antivirus, so we are safe” – without policies and updates it is an illusion.
• No collective document with licenses (problems with inspection or audit).

Day 21-30: 3-2-1 Backup, Website and Procedure Review
Objective: backups that it's possible reproducible; simple, secure website; procedural readiness.
Steps to follow:
Set parameters Ombudsman/RTO (how much data can you lose / how quickly can you get it back). Write it down in 2 sentences.
Implement 3-2-1 backup: 3 copies, 2 different media, 1 offline/immutability copy (also applies to M365).
Recreation test: restore sample file and mailbox – document the result.
Automatic backup reports: daily email "green/red" + person responsible.
Website: hosting with TLS, backups enabled, theme with updates, minimal set of plugins.
Cookies and privacy: correct consent banner, privacy policy, entrustment agreement with hosting (in practice this is "GDPR in a small company").
Analytics: GA4 with consent mode, Search Console – domain verification.
Procedure overview: offboarding, incident reporting, business continuity (backup power/internet, contact list).
Final result:
• Working 3-2-1 backup with recovery test, website with TLS and compliant cookie banner, set of minimum procedures.
How to check if it works:
• The backup report is sent daily; there are no “red” items for more than 24 hours.
• The restore test is successful and is described in one paragraph.
• The website passes a basic SSL test and loads quickly.
• GA4 only counts traffic after approval – and that's how it's supposed to be.
Two traps to avoid:
• “There are copies, but we have never tried to restore anything.”
• Cookies banner "for decoration" - incompatible with the tools actually used.
What's next?
- After 30 days you have the foundations in place: domain and email, stable network, legal licenses, basic security, working 3-2-1 backup and a compliant website. In the following chapters, we will expand on these areas and demonstrate the "why" by providing specific examples and mini-case studies from specific industries.

Company identity and email – the foundation of the work environment
A domain and business email are more than just an email address. Your business card on the internet – an element that builds credibility from the very first contact with a client or partner. In practice, your email address often serves as the starting point for assessing your company: whether it's professional and trustworthy.
Domain: selection and configuration
Which domain should I choose?
• Short, easy to remember, preferably in a format yourcompany.pl.
• Avoid complicated dashes and typos.
Why not free addresses?
Account type yourcompany@gmail.com undermines credibility. The client immediately notices the lack of professionalism and may ask, "Is this company truly legal?"Who to register with?
A must for company, not a private individual. You will avoid problems with domain transfers in the future.Renewals and inspection
Set reminders (e.g., in your company calendar) to ensure you don't forget to pay your annual fee. Losing your domain is one of the most common and costly mistakes.
Corporate Email: The Foundation of Communication
Choosing a mail system
The most frequently chosen solution is Microsoft 365 for BusinessWhy? Because in addition to email, you get a calendar, Teams, and shared files in OneDrive/SharePoint. It's a consistent work environment for the entire team.Main accounts and aliases
• Every employee should have personal account (e.g. jan.kowalski@twojafirma.pl).
• Type boxes office@, sale@, contact@ you can configure them as aliases or shared mailboxes – then you don't pay for additional licenses.
Mail security
To protect your domain reputation and avoid spam:• turn on SPF (determines which servers can send mail on behalf of your domain),
• add DKIM (digital signature of the message),
• set DMARC (rules on what to do with suspicious mail).
This sounds complicated to a non-technical person, but in practice it means one thing: your emails go to your inbox, not spam.
Employee Accounts and Password Policy
MFA (Multi-Factor Authentication)
Absolutely essential. In addition to a password, employees log in with an additional code from their phone or by app approval. This is a simple way to block 90% attacks on accounts.Password manager
Every user should have access to an application where they can save long, unique passwords. This solves the problem of sticky notes stuck to monitors.Password Policy
• Minimum 12 characters.
• Passwords do not need to be changed every month – it is better to focus on length and uniqueness.
• Change is necessary after a security incident.
Procedures and organization
Onboarding – when you hire a new person, you immediately set up an account for them, grant them access to files and set up MFA.
Offboarding – When someone leaves, the account must be locked the same day. Access to email and files passes to the manager.
Alias for the owner – it's good to have an account admin@yourcompany.pl as a central owner login with full permissions.
The final effect
Once your domain and email are configured correctly:
• all messages come from addresses in the company domain,
• emails do not end up in spam,
• each account has MFA and a secure password,
• employees use one consistent environment (Outlook, Teams, OneDrive),
• The employee entry and exit process is quick and secure.
We can set up and configure your domain, email, SPF/DKIM/DMARC, and MFA records. We'll also provide a short guide on how to manage employee accounts, ensuring your company's communications are professional and secure from day one.

Work equipment – laptops, monitors and peripherals without overpaying
Computer equipment is a work tool, not a luxury. Well-chosen computers, monitors, and accessories allow your team to work faster and more conveniently, while you avoid constant repairs and replacements. The key is matching equipment to the needs of roles in the company – not every employee needs the same laptop or set of accessories.
"Light office" vs. "Heavy office" – how to recognize the needs
Light office
• Work mainly in the browser, Word, Excel, email, Teams.
• All you need is a laptop with an i5/Ryzen 5 processor, 16 GB RAM and a 512 GB SSD.
• It is an ideal choice for administration, sales and customer service departments.
Heavy office
• Handling large files (e.g. CAD, graphics, video processing, Excel analyses with thousands of rows).
• Here it is better to aim for an i7/Ryzen 7 processor, 32 GB RAM, 1 TB SSD, and sometimes an additional graphics card.
• Such equipment will be useful in design offices, manufacturing companies or marketing.
Application: Instead of buying everyone the most expensive laptops, it's better to choose one that's suited to their role. This way, you control costs and everyone gets exactly what they need.
Monitors and work comfort
Why does a monitor matter?
A larger screen means greater productivity. Employees don't experience eye strain and waste time switching windows.Standard in the office
• 2 monitors 24-27 inches (Full HD or QHD).
• Height and angle adjustment (ergonomics).
• Alternatively: one 34-inch ultrawide for people who analyze a lot of data or projects.
Docking
• The docking station allows you to connect all your accessories with a single USB-C cable.
• This is especially important when working hybrid – you connect your laptop and immediately have monitors, a keyboard, a mouse and wired internet.
Peripherals and accessories
Keyboard and mouse
• Choose from corded or cordless models with a rechargeable battery.
• It is worth considering ergonomic versions for people who work several hours a day at the computer.
Headphones with microphone
• Teams, Zoom and Google Meet are commonplace today.
• USB-C or Bluetooth headsets with noise reduction allow you to talk without interruptions, even in an open office.
Webcam
• In laptops it is often average.
• An external Full HD camera costs several hundred zlotys, and the difference in the quality of online meetings is huge.
Power supplies and spare accessories
• It is worth having additional power supplies in conference rooms.
• Spare mice or keyboards come in handy in emergency situations.
Warranty and equipment life cycle
Why is it worth paying extra for the on-site/NBD (Next Business Day) guarantee?
• The service comes to the office and repairs the equipment on site.
• There is no problem with sending your laptop to a repair shop for weeks.
Hardware life cycle
• It is worth assuming that office laptops are replaced every 3-4 years.
• This means you don't work on outdated machines, and systems (e.g. Windows 11) run smoothly and without compatibility issues.
Disk Encryption and Asset Tag
• Every laptop should have it turned on BitLocker (protects data in the event of theft).
• Asset Tag (sticker with inventory number) facilitates equipment management and inventory.
How to avoid overpaying?
• Don't buy equipment "just in case." It's better to have a clear plan for replacing it every few years than to spend too much now.
• Check the total cost of ownership (TCO): purchase price + service + warranty + accessories.
• For smaller teams, it makes sense to buy a package (e.g. laptops + docks + monitors) from one supplier – you can often get a discount.
• Avoid the cheapest consumer models – the savings on purchase end sooner than you think (weaker battery, lack of company support).
The final effect
After selecting equipment according to roles in the company:
• each employee has a laptop tailored to their needs,
• workstations are ergonomic and comfortable,
• videoconferencing works without interruptions,
• the equipment is covered by a warranty and the replacement cycle is planned,
• Your data is protected by disk encryption.
We can help you choose laptops, monitors, and accessories to fit your budget and your team's workflow. We'll also handle encryption configuration, inventory, and workstation preparation to ensure they're up and running smoothly from day one.

Network and internet – router, Wi-Fi and order on the go
A stable and secure internet connection is essential for running a business. Even the best laptops and software won't help if your office video conference keeps crashing or a guest accidentally connects to the network where you store your company files. That's why it's worth taking the time to ensure this is the case right from the start. plan your router, Wi-Fi and network structure so that it works reliably and without surprises.
Main and backup link
Basic link
• Preferably optical fiber with symmetrical transfer (equally fast upload and download).
• Check the SLA (Service Level Agreement) guarantee – i.e. the contract stipulates how many hours per month the connection must be available.
Backup link
• The simplest solution: a router with an LTE/5G card that automatically switches to the backup when the fiber optic cable goes down.
• This is especially important if you work with online systems (e.g. cloud accounting, e-commerce).
Thanks to this arrangement, you will avoid company downtime, and employees will not even notice the operator's failure.
Router – the heart of the network
Why not a home router?
• Home devices do not have network segmentation options, are often less secure, and quickly become clogged with more users.
What should a business router have?
• VLAN (virtual network) support – separation of employee networks, guest networks and devices such as printers or IoT.
• Possibility of connecting backup internet (LTE/5G).
• Firewall with the ability to configure basic security rules.
• VPN option – secure access to the company network from home or on business trips.
Administrative access
• The password for the router panel must be unique and saved in the password manager.
• It is worth preparing simple documentation: the router's IP address, login details, VLAN description.
Wi-Fi in the office
Location of access points
• One router in the corner of the office isn't enough. It's better to install 2-3 Wi-Fi points to ensure a consistent signal.
• Avoid "dead zones" - it is worth doing a coverage test (there are free phone apps).
Separate networks (SSID)
• Company network (access to files, printers).
• Guest network (internet only, no access to internal resources).
• Optional network for IoT devices (e.g. cameras, air conditioners).
Passwords and security
• WPA3 or at least WPA2.
• Change your guest network passwords periodically.
• Never share the password to the main network with employees – they have access through their Microsoft 365 and Intune accounts.
Printers and additional devices
Printers, scanners, and other network devices should be connected to a separate VLAN. Why? This is often the weakest point in a network – manufacturers don't always update their software.
• Scan to email – set up documents to be sent directly to your email address or to a SharePoint folder.
• Printout security – PIN printout (the employee receives it only after entering the code at the printer).
• Reports and logs – many printers allow you to see who printed what – this increases control.
The final effect
Once the network is properly configured:
• you have a fast and stable connection, and in the event of a failure, the Internet works from a backup source,
• the router and Wi-Fi are secure, and guests only use their own network,
• printers and other devices do not expose company data,
• you have simple documentation with passwords and a network map, which facilitates operation and possible servicing.
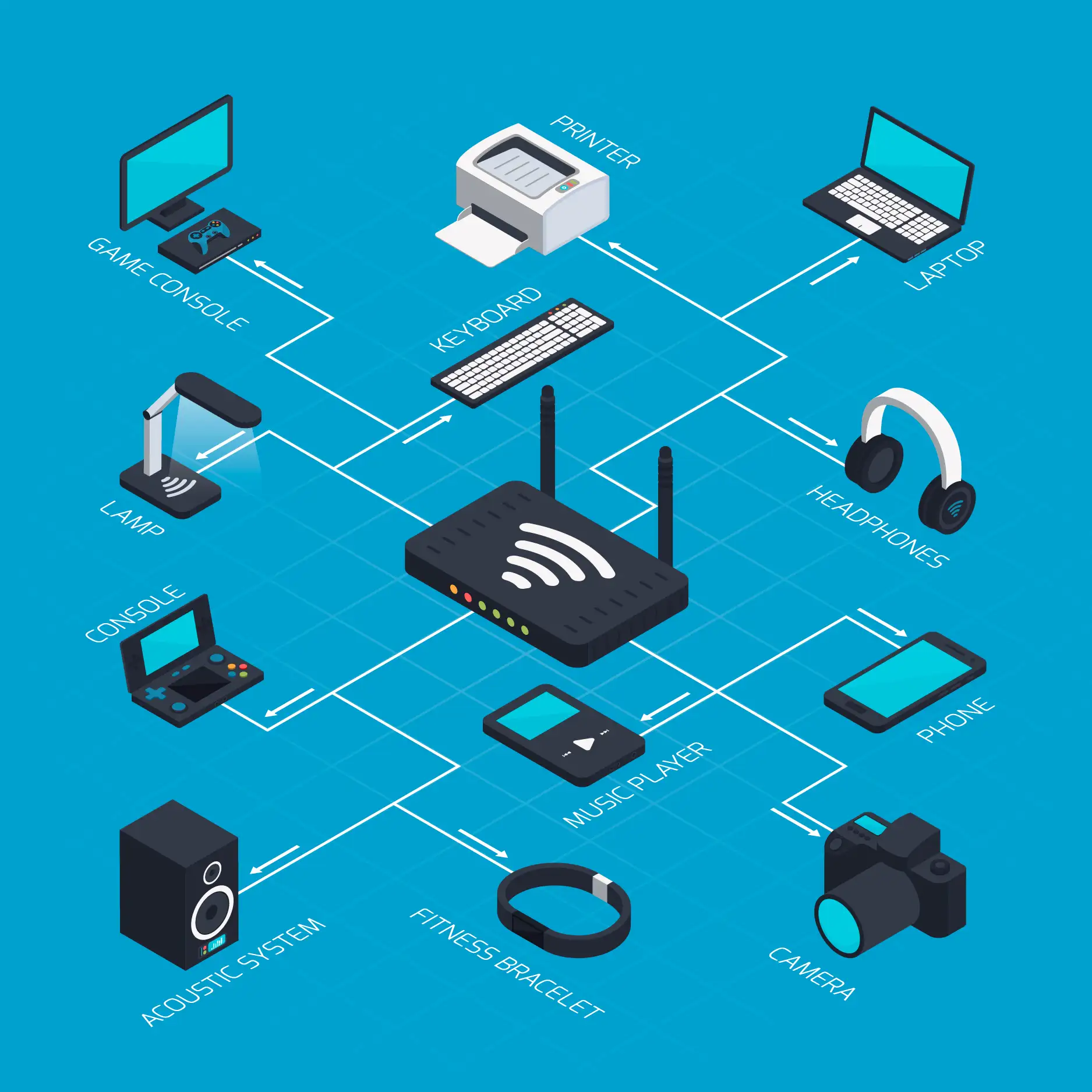
Software and licenses – what is worth buying to start?
Good hardware and a network are one thing, but without the right software, your business won't be able to operate efficiently and legally. Choosing startup software is a common dilemma: which packages are mandatory, and which are worth investing in later? This chapter answers that question in a simple and practical way.
The operating system – the foundation of everyday work
Windows 11 as standard
• New computers come with Windows 11 and it's worth investing in.
• Windows 10 is no longer supported October 14, 2025 – there will be no more security updates after this date.
• You can purchase additional support (ESU), but this is a temporary and expensive solution.
Why is it important?
The lack of security updates is a real threat – cyberattacks most often exploit vulnerabilities in old systems.
Microsoft 365 – office suite and work environment
This is currently the most popular solution for small and medium-sized businesses. A single subscription includes: corporate email, calendar, Teams, Word, Excel, PowerPoint, and file-sharing space.
Business Basic
• Online applications only (Word, Excel in browser).
• Corporate email and Teams.
• A good solution for administrative roles or people who don't need to install programs on their computer.
Business Standard
• Same as Basic + full versions of desktop applications (Word, Excel, Outlook).
• The most frequently chosen plan because it offers the convenience of working offline and online.
Business Premium
Includes everything from Standard, plus security and device management:
• Microsoft Intune (central management of computers and telephones),
• Defender for Business (protection against viruses and attacks),
• Entra ID P1 (advanced login and access control).
We especially recommend this plan to companies that want to immediately set a high level of IT security.
Practical advice: Often the best solution is a mix – some employees on Standard, and those responsible for data and finance on Premium.
Additional and industry-specific programs
E-signature and qualified signature
• Indispensable in many industries: accounting, HR, law, contract management.
• It is worth buying at the beginning – it will be useful when signing contracts or sending documents to the Social Insurance Institution or the tax office.
Industry programs
• Accounting: e.g. Symfonia, enova, Comarch ERP.
• Graphics and design: AutoCAD, Adobe.
• E-commerce: payment integrators, warehouse systems.
• Each of these programs requires a legal license, often a subscription.
Legality audit and software
Why is this so important?
Using illegal software can result not only in financial penalties but also in the confiscation of your hardware. It's a good idea to get all your licenses in order right from the start.
How to do it practically?
• Create a table with a list: program, license number, purchase date, invoice.
• Save your data in a safe place (e.g. SharePoint).
• Do an audit once a year – check if your licenses are still valid.
The final effect
Once the software is selected and implemented:
• Your employees use legal, up-to-date tools,
• you have control over who uses which license,
• you don't risk fines or loss of equipment,
• Your company operates in a consistent and safe work environment from day one.

Safety in practice – the minimum that makes real sense
Many companies treat IT security as something to deal with "later." Unfortunately, this is a common mistake – phishing attacks, data loss, or laptop theft can occur on the very first day of operations. Therefore, it's worth building a basic security suite that doesn't require major investments and protects against most common threats.
8 Security Policies You Can Implement in a Week
MFA (two-factor authentication)
• Each employee logs in not only with a password, but also with an additional code from their phone or hardware key.
• This simple setting blocks most account attacks.
System and application updates
• Computers and phones should install patches automatically.
• It is outdated systems that are most often exploited by cybercriminals.
Endpoint Protection (EDR)
• Traditional antivirus is not enough.
• EDR (e.g. Microsoft Defender for Business in the M365 Premium package) responds to unusual behavior – e.g. file encryption by ransomware.
Restriction of permissions
• An employee should not be the administrator of his or her computer.
• Program installation is performed centrally by IT, which reduces chaos and risk.
Macro and attachment blocking
• Many attacks start with a Word or Excel file with a suspicious macro.
• It's better to block them globally and enable them only for trusted sources.
Disk encryption
• Enable BitLocker on laptops and FileVault on Macs.
• This means that if the equipment is stolen, the data is useless to the thief.
Data access rules
• We divide files into departmental directories, and each employee has access only to what they need for their work.
• This reduces the risk of accidental deletion or disclosure of data.
Phishing training
• A short presentation or email test that shows what a suspicious message looks like.
• An employee who knows what to watch out for is often the best bulwark.
Device Management – Intune in Practice
Microsoft Intune allows you to set central security policies:
• forces a PIN or password on your work phone,
• blocks the installation of unauthorized applications,
• allows you to remotely erase data from your laptop or phone in the event of theft.
This gives you control over your equipment and data, even when your employees are working remotely.
BYOD or company equipment?
• BYOD (Bring Your Own Device) – the employee uses their own laptop or phone. This is cheaper but more difficult to secure.
• Company equipment – full control over devices, the possibility of quick service, implementation of policies and encryption.
It's better to start with company-owned hardware. This allows you to avoid issues with security and data ownership.
The final effect
Once the above minimum is implemented:
• every company account has MFA and a strong password,
• all devices are up to date and protected by EDR,
• data on laptops is encrypted,
• every employee knows how to recognize a suspicious email,
• If your equipment is stolen, you can remotely wipe your data.
It is this level of security that reduces the risk of a serious incident several times over, giving you peace of mind.
Backup 3-2-1 – copies that can truly be restored
Backups are one of those things that most companies put off until they lose important data. Therefore, it's best to understand the simple 3-2-1 rule right away and implement it from day one.
What does the 3-2-1 rule mean?
• 3 copies of data – one main and two spare.
• 2 different media – e.g. local disk and cloud.
• 1 offline copy – disconnected from the Internet or protected against overwriting.
This arrangement protects you even if one system fails or a ransomware attack occurs.
Backup Microsoft 365 and company data
Many business owners assume that files in OneDrive or email in Outlook are already backups. Unfortunately, this is only retention, which is storing data for a specified period of time. If someone accidentally deletes a file and the retention period expires, the data is lost.
That's why it's worth implementing external Microsoft 365 backup (mail, OneDrive, SharePoint), which makes automatic copies and allows for quick restoration of individual messages or documents.
How to test copies?
A backup only makes sense if it can be restored. Therefore:
• do it every quarter recovery test (e.g. restore one file and one mailbox),
• check if the recovery time (RTO) and the amount of data lost (RPO) are acceptable to you.
Common mistakes worth avoiding
One copy on the same disk as production data.
Backup without testing – works only “on paper”.
No offline copies – in the event of a ransomware attack, all files may be encrypted.
The final effect
Thanks to the 3-2-1 rule, you can be sure that even in the event of a failure, employee error or hacker attack, your data is safe and can be quickly restored.

A website for starters – safe, fast and compliant
For many customers, your website will be their first contact with your company. It's a digital business card that should be simple, fast, and legally compliant. It doesn't have to be a complex portal – the important thing is that it operates stably, presents your offerings, and inspires trust.
Hosting and TLS certificate
Hosting
• Choose a proven provider with servers in the EU (this is important for GDPR).
• Pay attention to the SLA (service availability) and backups included in the package.
TLS Certificate (https://)
• Absolutely basic – the lack of a certificate looks unprofessional today.
• Many hosting companies offer free Let's Encrypt certificates.
With TLS, your website has a green padlock in your browser and customer data (e.g. forms) is encrypted.
CMS and plugins
WordPress or other CMS?
• The most popular choice is WordPress – simple, cheap, with a huge number of templates.
• It is important not to overdo it with the number of plugins – each additional plugin is a potential security hole.
Updates
• CMS and plugins need to be updated regularly update.
• Lack of updates is one of the main reasons why company websites are hacked.
Cookies and GDPR
Consent banner
• If you use analytical tools (e.g. Google Analytics) or tracking plugins, you must display the cookie banner.
• The banner should allow acceptance and rejection cookies – just “OK” is not enough.
Privacy Policy
• It should clearly state what data you collect and for what purpose.
• It's worth having it ready before publishing the website.
Data processing agreement
• If the hosting provider processes data (e.g. contact forms), sign a data processing agreement with them in accordance with the GDPR.
Basics of analytics and visibility
Google Analytics 4
• Allows you to analyze website traffic.
• Please note that it only works correctly if the user consents in the cookie banner.
Google Search Console
• A free tool to monitor whether your website is visible in Google search.
• Thanks to it, you will find out what phrases attract visitors.
The final effect
Your website:
• works fast and is available 24/7,
• has a TLS certificate and looks professional,
• meets GDPR requirements (cookie banner, privacy policy),
• is updated and protected against typical attacks,
• gives you data on traffic and visibility on Google.

Law and Compliance (PL) – the most important obligations without the jargon
IT law may sound complicated, but in practice, it boils down to a few basic obligations. Implementing these from the start will help you avoid audit issues and gain peace of mind.
GDPR in a small business
Data processing agreements
• If you use external services (e.g. hosting, Microsoft 365), sign a data processing agreement.
• This is a simple document that regulates that the supplier processes data in accordance with the GDPR.
Record of processing activities
• List of what data you collect and for what purpose (e.g. customer data, invoices).
• A simple Excel table is enough.
Data Protection Officer (DPO)
• Only mandatory in larger companies or if you process sensitive data on a large scale (e.g. medical data).
KSeF – National e-Invoice System
• Mandatory for companies from 2026.
• It is worth organizing your invoice numbering now and checking whether your accounting software allows integration with KSeF.
• This is not only a legal requirement, but also an opportunity to automate document flow.
Software legality
• All programs must be licensed.
• No license = risk of financial penalty and even equipment seizure during the proceedings.
• Solution: Keep invoices and license numbers in one easily accessible table (e.g. SharePoint).
System security
• The operating system and programs must be up to date.
• Windows 10 will not be supported after October 14, 2025 – it is worth planning to switch to Windows 11.
The final effect
After implementing the basic principles:
• Your company operates in accordance with the GDPR,
• you are prepared for KSeF,
• all programs are legal and documented,
• systems are up to date and secure.

Budget and priorities – what comes first and how much?
When starting a business, budgets are usually limited, so prioritizing is key. You don't have to buy everything at once—it's important to invest first in what secures the business and enables the team to work.
1. First of all
Domain and company email
• Cost: approx. PLN 50–100 per year for a domain + from PLN 20 per month per user in Microsoft 365 (Business Basic).
• Result: professional communication and central account management.
Equipment for employees
• Office laptop (light office): from PLN 2,800–3,500 net.
• More efficient laptop (heavy office): PLN 4,500–6,500 net.
• Monitor 24–27″: PLN 700–1000.
• Docking station: 400–700 PLN.
Router and Wi-Fi network
• Business router with VLAN support: from PLN 1,000.
• Wi-Fi access point: PLN 500–800 per unit.
• LTE/5G backup link: subscription from PLN 30–50 per month.
Microsoft 365 and licenses
• Business Basic: approx. PLN 20 net/user/month
• Business Standard: approx. PLN 50 net/user/month
• Business Premium (security, Intune, Defender): approx. PLN 90 net/user/month
Backup 3-2-1
• M365 Backup (mail, OneDrive, SharePoint): from PLN 10–15 per user per month.
• Additional local copy (e.g. NAS drive + cloud): from PLN 1,500 one-time + PLN 50–100 per month for cloud storage.
2. What to implement in the second step (30-90 days)
• Website with TLS and backup: from PLN 1,500–3,000 for a simple business card website.
• Security and GDPR Procedures Training: from PLN 500 (one-off for a small team).
• Additional accessories (headphones with microphone, cameras): PLN 300–600 per position.
• Qualified e-signature: approx. PLN 300–400 per year.
3. How to plan your budget wisely
• CAPEX (one-off investments): laptops, routers, monitors, printers.
• OPEX (monthly costs): Microsoft 365 licenses, backup, internet.
For example, for a 5-person company (3x Standard, 2x Premium) the monthly cost of licenses and backups is:
• 3x M365 Standard (50 PLN) = 150 PLN,
• 2x M365 Premium (90 PLN) = 180 PLN,
- • Backup (5x 15 PLN) = 75 PLN,
Total: approx. PLN 405 per month for work environment and safety.
4. Where it is not worth saving
• Security (MFA, EDR, backup) – cheaper solutions often result in greater losses in the event of an incident.
• Office equipment – the cheapest laptop or home router will quickly prove to be insufficient.
• Legal licenses – the risk of punishment and loss of reputation is disproportionate to the savings.
5. Where you can optimize costs
• Combining different Microsoft 365 plans (some employees on Standard, some on Premium).
• Purchase monitors and accessories in a package from one supplier.
• Outsourcing IT instead of hiring a full-time IT specialist at the start.
The final effect
After this approach you have a clear plan:
• you know how much you spend in the first month and in the following months,
• you first invest in the foundations (domain, email, hardware, licenses, backup),
• you can spread the remaining costs over the following quarters,
• you avoid burning your budget on unnecessary solutions.
We can prepare a customized IT startup budget plan for you, including hardware, license, and backup costs. This way, you'll know exactly how much to invest in the first month and what to postpone.

Case studies – what MUST work in industries (and what is worth investing in)
Every industry has its own specific IT needs. Below, you'll find short, practical examples demonstrating what "must-haves" and "worth-investing" look like for different types of companies. This will help you identify which solutions will be crucial for your business.
Transport, forwarding, logistics (TSL)
Must work:
• Permanent company email and Teams for communication with drivers and customers.
• Printers and scanners for fast processing of transport documents.
• Stable internet with LTE backup – a connection failure in the office means work stoppage.
It's worth investing in:
• Mobile device management (MDM/Intune) to keep drivers' phones protected.
• Automation of document flow – e.g. transport orders or invoices.
Production and small plants
Must work:
• Wired network in the hall and Wi-Fi in the office, separated by VLANs.
• Workstations for operating machines, ERP systems or quality files.
• Regular file server backups – documentation and projects must be protected.
It's worth investing in:
• Separate network for IoT machines (sensors, production lines).
• IT monitoring (alerts about network or server failure).
E-commerce and online stores
Must work:
• Store hosting with TLS certificate and high availability.
• Payment and warehouse system integration.
• Backup of database and product files.
It's worth investing in:
• WAF (Web Application Firewall) protecting the store against attacks.
• CDN (Content Delivery Network) to ensure the website runs quickly throughout Poland and beyond.
• Uptime monitoring – quick notifications if the store goes down.
Accounting office
Must work:
• E-signature and qualified certificate.
• Secure document exchange with clients (e.g. folders in OneDrive).
• Regular backups of databases and accounting programs.
It's worth investing in:
• Microsoft 365 Business Premium (Defender, Intune, Entra ID P1).
• Laptop disk encryption and document security policies.
Medical office and health services
Must work:
• Patient registration and appointment calendar.
• Encryption of computer disks and documentation backups.
• GDPR procedure (patient specific data).
It's worth investing in:
• Network segmentation (separation of reception computers from medical devices).
• Access audit – who viewed the documentation and when.
Construction and design services
Must work:
• Licenses for design programs (e.g. AutoCAD).
• Powerful laptops with a graphics card and a large amount of RAM.
• Regular backup of projects on external drives and in the cloud.
It's worth investing in:
• File versioning – the ability to revert to an older version of the project.
• Cloud for sharing files with clients and subcontractors.
Law firm
Must work:
• Business email with full TLS encryption.
• Secure storage of documents and contracts.
• Regular backup of cases and client files.
It's worth investing in:
• Email encryption (e.g. S/MIME certificates).
• Data classification – separating confidential documents from the rest.
Gastronomy and retail (stationary stores)
Must work:
• Stable operation of POS systems (cash registers, payment terminals).
• Wi-Fi network separated for customers and sales systems.
• Backup LTE in case of internet failure.
It's worth investing in:
• POS system monitoring and error reporting.
• Sales database backup – even one day of lost data is a big loss.
While each industry differs in details, one thing is common: communication, backup and security must workThe rest are investments that increase convenience, automation, and competitive advantage. We can prepare a customized audit for your industry and provide a list of "must-haves" and "worth-investing" solutions. This will give you a clear IT action plan tailored to your company's specific needs.

The Most Common IT Startup Mistakes (and How to Avoid Them)
Beginning entrepreneurs often try to save money on IT or postpone decisions until later. Unfortunately, this is when problems arise that can paralyze the company. Below, you'll find 10 common mistakes and simple ways to avoid them.
1. No MFA on accounts
Problem: employees log in only with a password that is easy to crack.
Solution: enable Multi-Factor Authentication in Microsoft 365 and all critical services.
2. One home router for the entire company
Problem: lack of network segmentation, vulnerability to attacks and drops in connection quality.
Solution: choose a business router with VLAN and backup LTE.
3. No offline copy
Problem: a copy of data kept on the same disk as the original.
Solution: Use the 3-2-1 backup rule, including one offline or cloud copy.
4. Backups without testing
Problem: the backup exists only "on paper" - restoration does not work.
Solution: Run a file and mailbox recovery test quarterly.
5. Trial licenses without invoice
Problem: using software without a full license.
Solution: store all invoices and license numbers in one table (e.g. in SharePoint).
6. No data processing agreements
Problem: hosting or email provider processes customer data without a formal basis.
Solution: sign a data processing agreement with each entity that handles your data.
7. Shared network for employees and guests
Problem: a guest may have access to company files or printers.
Solution: create separate SSIDs (Wi-Fi networks) – one for employees, one for guests.
8. No offboarding procedure
Problem: the former employee still has access to email or files.
Solution: prepare a checklist – blocking the account, transferring files, taking away equipment.
9. No legal cookie banner
Problem: the website collects analytical data without proper user consent.
Solution: implement a GDPR-compliant cookie banner (acceptance and rejection).
10. No plan to migrate from Windows 10
Problem: After October 14, 2025, the system will lose security support.
Solution: Plan to gradually transition to Windows 11 or new hardware with this system.
The final effect
Avoiding these mistakes:
• Your company operates safely and stably,
• you don't risk penalties for lack of a license or GDPR violations,
• you don't lose data or access to services at critical moments.
Frequently asked questions
What is best to invest in first: hardware, licenses or a website?
How much does “start-up IT” actually cost for a small company?
How to prepare for KSeF, since the obligation will only come into force in 2026?
Do I need a Data Protection Officer (DPO) in a small company?
What safety procedures are worth having written down right away?
What happens if I forget to renew my domain or TLS certificate?
Summary – The Next Step for Your Business
Starting a business is a time when IT should be your ally, not your hindrance. In this guide, I've shown you step-by-step what to consider: from domain and company email, through hardware, network, and licenses, to security, backup, and regulatory compliance. I've also included examples from various industries to help you see what really MUST work for your company and what's worth investing in next.
The most important thing to remember:
• the foundation is professional email, secure login and data backup,
• hardware and software must be adapted to the role of employees – not to everyone in the same way,
• It is better to implement simple procedures and a proven 3-2-1 backup than to risk data loss,
• the law (GDPR, KSeF, license legality) does not have to be complicated – a few basic steps are enough to act in accordance with the regulations.
Thanks to this, you have a well-organized IT system from day one, which not only supports business development but also builds a professional image in the eyes of customers and partners.
If this topic applies to your company and you want your IT to be organized and secure from the start, contact us. We'll prepare a plan for you, implement key solutions, and ensure you can focus on growing your business.





