Over the past few years, cybersecurity has become a key topic for companies operating in the European Union. The number of cyberattacks is constantly growing, and their consequences can be catastrophic - both financially and in terms of image. It is no wonder that the EU has decided to tighten regulations on the security of networks and information systems.
One of the most important legal acts in this area is NIS Directive 2 (Network and Information Systems Directive 2), which is to replace the previous NIS Directive from 2016. The new regulations introduce a number of obligations for companies from various sectors - not only the largest ones, but also medium-sized and in some cases even small enterprises. What's more, failure to implement the NIS 2 requirements is subject to severe financial penalties that can seriously threaten the stability of the company.
For many entrepreneurs, the topic NIS 2 implementations sounds complicated. What exactly is this directive? Who does it cover? What obligations does it impose? And most importantly: how to ensure compliance with the regulations so as not to expose yourself to sanctions?
In this article you will find accessible but detailed explanation all key issues related to NIS 2. We will also show you how SimpleIT can help your company conduct an audit IT security, the development of appropriate policies and procedures, and the full implementation of the requirements of the Directive.

What is NIS Directive 2?
The NIS 2 Directive, or Network and Information Systems Directive 2, is a new European Union regulation that aims to significantly strengthen Enterprise Cybersecurity operating in the Member States. This is an update of the earlier NIS Directive from 2016, which was the first ever EU legislation on the security of network and information systems.
Why were the new regulations introduced? The digital world is changing at a rapid pace. The development of technology, the growing number of internet connections, remote work, cloud computing - all this creates not only huge opportunities, but also new threats. Cybercrime is becoming increasingly complex and costly, and existing regulations are no longer adequate to address current challenges.
The purpose of the NIS 2 directive
The main objective of NIS 2 is to raise the overall level of cyber resilience across the European Union. This means:
✅ increasing the level of protection of networks and IT systems,
✅ improving the exchange of information between Member States,
✅ strengthening the resilience of critical services (e.g. in the energy, health, transport sectors),
✅ ensuring effective response to serious cyber incidents.
What does NIS 2 change compared to the previous directive?
NIS Directive 2 is much more ambitious than its predecessor. It introduces a number of key changes, such as:
• Expanding the scope of entities covered by the regulations — not only the largest companies, but also medium-sized and even some small businesses if their activities are important to society.
• Uniform rules throughout the EU — previous regulations were implemented by member states in different ways, which caused chaos. NIS 2 focuses on harmonization of regulations.
• Increased requirements for risk management — companies must demonstrate much more advanced security procedures.
• Tougher financial sanctions for failure to fulfill obligations.
• Obligation to report serious incidents within a very short time (e.g. within 24 hours of detection).
Why is NIS 2 so important for businesses?
Although the NIS 2 Directive is EU law, in practice it means specific changes that must be introduced entrepreneurs in their organizations. This is not just “another paper obligation”, but real actions to protect the company from increasingly advanced digital threats.
Importantly, the NIS 2 Directive is not limited to the technological sphere - it also covers issues organizational (e.g. security policies, incident response procedures, employee training), which means that its implementation requires the involvement of not only IT departments, but also company management boards.
Who does the NIS 2 Directive apply to?
One of the biggest problems we see among business owners is uncertainty: Is my company subject to NIS 2? In this chapter we answer this question in detail, because knowing the scope of the directive is a key step before we start thinking about implementation.
Division into key and important entities
The NIS 2 Directive divides companies into two main categories:
• Essential entities — organizations that provide services of strategic importance for the functioning of society and the economy.
• Important entities — companies that, although not considered essential, still have a significant impact on digital security in Europe.
Each of these groups has its own set of responsibilities and is subject to supervision by state supervisory authorities.
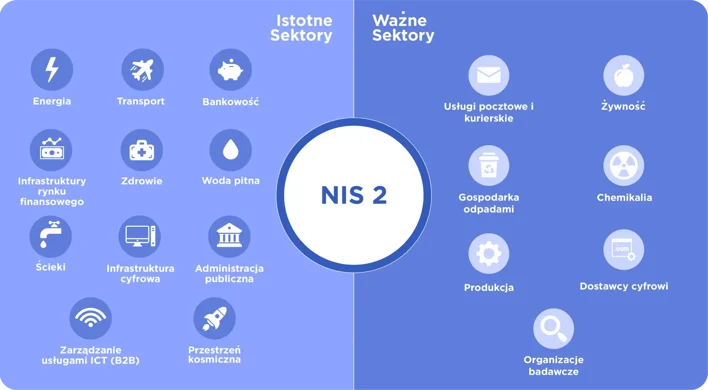
Sectors covered by NIS Directive 2
Key entities They operate, among others, in the following sectors:
• energy (electricity, gas, heat suppliers),
• transport (railways, airports, ports, public transport),
• health (hospitals, clinics, laboratories, suppliers of IT systems for healthcare),
• banking, financial market infrastructure,
• digital infrastructure (e.g. data centers, DNS providers),
• suppliers of drinking water and sewage.
Important entities for example:
• digital service providers (e-commerce, search engines, cloud platforms),
• manufacturers of key technologies (e.g. network devices),
• postal and courier service operators,
• waste managers, producers of certain goods.
Who exactly qualifies? Checklist for entrepreneurs
Here simple set of questions, which will help you assess whether your company is subject to NIS2:
🔹 Do you operate in one of the sectors mentioned?
🔹 Does your company employ at least 50 people? or achieves an annual turnover of over 10 million euros?
🔹 Does your company provide services that are important to public safety, the economy, or critical infrastructure?
🔹 Do your IT systems handle sensitive data or enable critical systems (e.g. in the health, energy sectors)?
If you answer "yes" to any of these questions, there is a very high probability that you are subject to NIS Directive 2.
How many companies in Poland will be affected by these regulations?
It is estimated that the NIS 2 directive will cover even 10,000 entities, which is a significant expansion compared to the previous NIS Directive. It is not just large corporations - a large part are medium and smaller enterprises that were not aware of the requirements related to Enterprise Cybersecurity.
By when do you have to adapt?
Every country had time until October 17, 2024, to introduce it into their national law – i.e. to prepare a law and regulations that will tell companies exactly what to do – Poland did not do this in time. As a result, the European Commission filed a lawsuit against Poland (and several other countries) a lawsuit to the Court of Justice of the EU for the delay. This is a form of pressure - the EU requires Poland to adopt the appropriate regulations as soon as possible. Currently, the draft act is at the stage of review and public consultation. Considering the standard pace of legislative work, it can be assumed that:
➡️ the regulations will come into force no later than the second half of 2025, and perhaps even faster if the pressure from the EU is strong enough,
➡️ once the law is passed, there probably won't be much time left to adapt - because companies should be ready almost immediately.
What to do now?
Although we do not yet have a Polish regulation, companies should not wait idly. Why? Because implementing NIS 2 is not something that can be done "overnight". It is a process that requires:
✅ IT systems audit
✅ review of procedures
✅ creating emergency plans
✅ team training
✅ and sometimes even replacing technologies or changing IT service providers.

Key obligations arising from NIS 2
For many entrepreneurs, the mere awareness that they are subject to the NIS 2 directive is just the beginning. The most important question is: What exactly needs to be done to comply with the new regulations? In this chapter we explain it step by step.
Risk assessment and risk management
Every company covered by NIS 2 is obliged to regularly analyze cybersecurity threats. It's not just about standard security measures like antivirus or firewalls - you need to carefully assess where the gaps may appear, what the potential attack scenarios are, and what their effects may be.
Examples of activities:
• Identification of key systems and data,
• Conducting risk analysis (e.g. IT security audit),
• Preparation of an action plan to minimize identified risks.
Technical and organizational measures
The company must implement both Technical, What organizational security to help protect its systems. What does that mean?
🔹 Technical measures: data encryption, incident monitoring and detection systems, access control, Backups, network security.
🔹 Organizational measures: security policies, incident response procedures, test schedules, team training.
It is important to remember that Enterprise Cybersecurity It doesn’t end with technology – the preparation of people plays a huge role.
Incident reporting
If a serious incident occurs in a company (e.g. ransomware attack, data leak, critical system failure), the NIS 2 Directive imposes an obligation to promptly report this fact to the relevant supervisory authorities.
What does the process look like?
• Pre-registration within 24 hours from the detection of an incident,
• Detailed report within 72 hours,
• Final report upon completion of internal investigation.
Importantly, companies must be prepared clear procedures, who is responsible for reporting incidents, how to collect data and what information should be provided to state authorities.
Maintaining business continuity
The directive requires organizations to have a contingency plan in place so that in the event of an incident, they can quickly restore key services. This means creating procedures such as:
• Disaster Recovery Plan,
• Business Continuity Plan.
Regular audits and updates
NIS 2 compliance is not a one-time implementation of procedures. Companies must regularly:
• conduct IT security audits,
• update its policies, procedures and systems,
• respond to changing threats (e.g. new types of attacks, vulnerabilities).
Training for employees
Let's not forget about the human factor! Employees are often the weakest link in a cybersecurity system. That's why NIS 2 requires:
• organization of cybersecurity training,
• building awareness of threats (e.g. phishing, social engineering),
• establishing clear rules for the use of IT systems.
Sanctions and responsibility
Failure to comply with the obligations arising from NIS 2 may result in:
⚠️ Financial penalties - for key entities up to 10 million euros or 2% annual turnover,
⚠️ Responsibility of board members who should oversee the organization's compliance with the directive.
This is important: implementing NIS 2 is not just a task for IT department - that the responsibility of the entire organization, including the board.

Summary
As you can see, implementing the NIS 2 directive is not a simple matter of checking off a few formalities. It is a complex process that includes IT security audit, risk analysis, implementation of procedures, preparation of documentation, as well as training the entire team.
This is where it comes in SimpleIT. Our goal is to help companies navigate all stages of cybersecurity and new regulations.
What do we offer?
✅ Full IT Security Audit — we’ll identify pain points in your company’s IT infrastructure before cybercriminals do.
✅ Implementation of NIS 2 compliant policies and procedures — we will prepare not only documents, but also practical solutions.
✅ Assistance in creating emergency plans and incident reporting procedures — so that your company can operate efficiently even in times of crisis.
✅ Training for employees — we will build awareness of cyber threats across the entire team.
✅ IT outsourcing and ongoing support — if you don't have your own IT department, we can take over some of the tasks, giving you peace of mind and security.
Thanks to our experience and knowledge of regulations, we will make sure that your company is fully prepared for the new challenges related to Enterprise Cybersecurity.
If you want to find out how we can tailor our services to your needs, contact us today. We offer a free consultation during which we will assess what actions are needed in your case.





