Imagine receiving an email that looks like a regular message from a friend, a business partner, or someone who knows a surprising amount about you. It doesn't contain a virus, doesn't have a suspicious attachment, and yet, that one click could open the door to your files, accounts, company data, and image.
That's how it works phishing – one of the most effective and frequently used methods of email fraud. You don't have to be a casual user to fall for it. On the contrary, the more trustworthy the email appears, the greater the chance of falling for it.
In this article I will show you a real example of a phishing emailthat you can receive as an individual or entrepreneur. We'll break it down and you'll learn, how to recognize phishingbefore you can click on anything suspicious.
You will learn:
• what does a typical one look like phishing message,
• what tricks do cybercriminals use,
• how to defend yourself and company against phishing,
• and what to do if a suspicious email has already arrived in your inbox.
Whether you run a sole proprietorship, manage a team, or simply want to protect your email account, this knowledge can save you from major problems.
We'll begin with a case study. Here's a message that was intended to blackmail someone into extorting €1,300 – please read it carefully.
What does a real phishing email look like?
At first glance, it's an ordinary email—no strange links, no suspicious attachments, no glaring errors. But its content was written with full premeditation to induce fear, pressure, and guilt. This is precisely how phishing scams work—their strength lies not in sophisticated technology, but in psychology and manipulation.
Below is an example of a real message that reached one of our users. The purpose of the message was to: extorting money in exchange for allegedly not publishing compromising material.
Below is the content of the message (unchanged, except for numbering added for analysis):
1) Hi!
As you can see, this is not a formal email, but unfortunately that does not mean anything good for you.
BUT don't panic, it's nothing serious. I'll explain everything to you now.2) I have access to your electronic devices, which are part of the local network you regularly use. I've been tracking your activity for the past few months.
3) How did it happen?
You visited hacked sites with bugs that I exploited with my software (which I bought from Darknet specialists).
This is very complex software that acts like a Trojan horse. It updates regularly, so your antivirus software can't detect it.
This program has a keylogger; it can turn on your camera and microphone, send files, and give access to your local network.4) It took me a while to access information from other devices, now I have all your contacts with conversations,
information about locations, what you like, your favorite websites, etc.
Honestly, I didn't mean anything bad by it at first; I just did it for fun. It's my hobby.5) But I caught COVID and unfortunately lost my job.
So I figured out how to use “my hobby” to get money from you!
I recorded a video of you masturbating. This video has a separate screen where you're easily recognized, and it also clearly shows what kind of videos you prefer.
Well, I'm not proud of it, but I need money to survive.6) Let's make a deal. You pay me whatever I need, and I won't send this video to your friends, family, and coworkers.
You should understand that this isn't a joke. I can send this via email, text message, social media, and even to the media (I've hacked some of their admin accounts).
So you could become a Twitter or Instagram “star”!7) To avoid this, you should send me 1300 EUR in Bitcoins to my BTC wallet: 17q...
8) If you don't know how to use Bitcoin, search Bing or Google for "how can I buy Bitcoin" or something like that.
I will delete this video as soon as I receive my money. I will also remove the malware from your devices, and you will never hear from me again.
I'll give you two days, which is plenty, I think. The clock will start ticking as soon as you open this email. I'm monitoring it!9) One more thing:
There is no point in reporting this to the police because I use TOR, so there is no way to trace the Bitcoin transaction.
Don't reply to me (I generated this letter on your account and gave you the real address of someone who has no clue about it). This way, I can't be traced.10) If you do something stupid or goes against my expectations, I will immediately share the video.
Good luck!
Step by step analysis – what's wrong here?
1) Emotional manipulation (fear and relief)
First, there's tension ("this doesn't mean anything good for you"), followed by momentary relief ("but don't panic..."). This is a common mechanism used in scams.
2) False claim of device hacking
There's no evidence of a breach—it's a bluff designed to cause panic. The scammers have no access, but they're counting on the victim to believe them.
3) Technobabble meant to sound professional
Mentions of "Trojan Horse," "Darknet," and "keylogger" are intended to sound professional, but they are vague and unspecific. This is typical of phishing—the goal is to scare people, not provide facts.
4) Bluff about access to contacts and location
Lack of evidence – the scammer uses general phrases that apply to everyone. "Favorite websites," "locations" – it's just a psychological game to make the victim think, "Maybe they actually know something?"
5) Emotional justification and erotic blackmail (so-called sextortion)
The popular cliché: "I have camera footage, you pay or I'll share it." In 99% cases, this is complete fiction. There was no video, no camera – it's pure fiction. manipulation.
6) Threats and pressure
"I'll send it to family, friends, the media..." – exaggeration and intimidation. Scammers know that many people fear social embarrassment most.
7) Request payment in Bitcoins
Classic warning signal – if someone requests payment in cryptocurrencies, we are almost certainly dealing with fraud. The anonymity of the transaction is the only reason for this choice.
8) Request to make the victim responsible for "ending the matter"
"Pay me, and I'll disappear." This creates a false sense of control—the victim believes they have control over the situation. In reality: pay me → you'll be marked as an easy victim → you'll receive further demands.
9) Cut off from help
Trying to prevent reporting: "TOR, no way to trace it, it won't help." This is a bluff – it's worth reporting every fraud attempt (e.g., to CERT Polska, CSIRT NASK, or the police).
10) The final threat – the panic mechanism
“You do something stupid, I'll share the video.” A hollow threat intended to force immediate action and block logical thinking.
What you see above is not a random email from a generator, but a deliberate attempt to extort money based on psychological blackmail. These types of phishing scams are becoming increasingly difficult to spot – especially for people unfamiliar with how cybercriminals operate.
So if you know someone – a parent, grandparent, cousin – who uses the internet but doesn't feel confident using it...
Show him this article.
This may be the first step to protecting your loved ones from losing money, privacy, or peace of mind.

8 Characteristics of Typical Phishing Emails
While the content of phishing emails may vary, most follow very similar patterns. In this section, we'll show you the most common warning signs—the so-called red flagswhich should set off a red flag in your head.
Recognizing them in time allows avoid costly email fraud – whether in your personal life or in your business. Here are 8 elements that often appear in phishing emails:
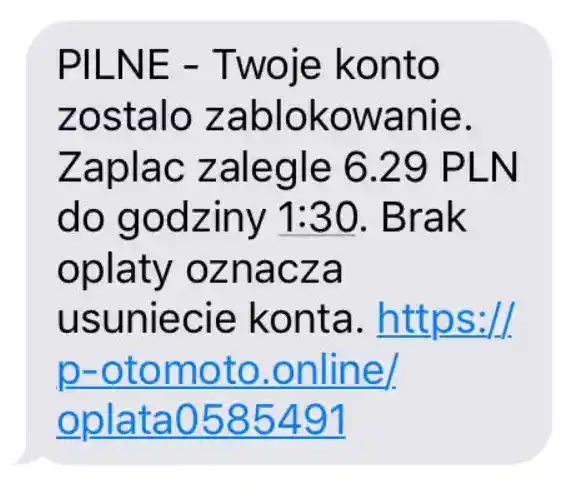
1. Urgent tone and threats
The scammer wants you to act impulsively. Hence phrases like:
"You have 2 days", "The clock is ticking", "If you don't pay, the film will go to everyone".
This is an attempt to block logical thinking. Phishing works when the victim is in a hurry.
2. False technical information
Many such messages contain technobabble: alleged malware, camera access, eavesdropping, etc.
There is no evidence there – it is pure psychological game. Proven phishing example: false claims about "Trojan horse" or "network monitoring"
3. Linguistic errors and strange syntax
Most phishing emails contain typical errors – typos, strange punctuation, unnatural wording.
Not because they are automatically translated – but because they have catch only those people who are easy to manipulate.
This is the so-called selection of "easy targets."
4. Fake real life stories
Emotional stories often appear: "I lost my job", "I need money for treatment", "I'm doing this out of necessity".
This type email scam It's meant to arouse sympathy and lower your guard.
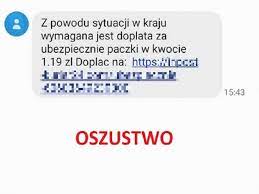
5. Requests for payment in Bitcoin or another anonymous system
If someone requests a transfer in cryptocurrency, it is almost always a sign that phishing message does not come from a real institution or person.
Phishing in the company it often takes this form - from the address of the "boss" or "IT department" with a request for an immediate transfer
6. No personalization
“Hello”, “Dear user”, “Customer” – these are very general phrases that do not contain your name or any unique data.
Most phishing emails are sent in bulk, so scammers don't know your identity – and that often gives them away.
7. Unusual sender or email address
Email address does not match the official domain, contains strange characters, or looks suspicious:
e.g. support-amazn.com, admin_pay-pal@securemail.ru.
Pay attention to domain endings – even a small typo is a red flag.
8. Requests to keep secret or not contact anyone
“Don’t answer,” “Don’t tell anyone,” “Don’t report it to the police” – these are classic attempts to isolate the victim.
It's worth remembering: If someone suggests that you should not tell anyone about the message, it is most likely an attempt at fraud.
Remember:
The more of these elements appear in one message, the more likely it is that phishing messageIf you have any doubts, it's better to ask a specialist than to take risks.
Our company offers IT support for companies – including analyzing suspicious messages, configuring anti-phishing filters, and providing employee training. We're here to support you if needed.

What to do when you receive a message like this?
Receiving a phishing email can be unsettling, especially if it involves blackmail, false accusations, or threats. But remember: it is a deliberate act by a fraudster who tries to evoke an emotional response, not the actual threat. Instead of acting impulsively, proceed step by step.
Below you will find instructions on how to respond safely and effectively, both as an individual and on behalf of the company.
Step 1: Do not reply to the message
No matter what the message says – do not click "Reply", do not write explanations or threats, do not engage in discussionsAny form of response shows that your address is active, which may encourage scammers to continue their activities.
Step 2: Don't click on links or attachments
Even if the message looks credible and the sender is impersonating a bank, office or IT employee, for example – do not click on any links or open any filesIf in doubt, visit the institution's website. manually in the browser, not from email.
Step 3: Take a screenshot
Save the content of the message in a safe way - preferably as screenshot, so you can retain the original wording, sender's address, and any linguistic errors. This material may be useful when reporting a case.
Step 4: Mark the message as phishing/spam
Most email programs (e.g. Outlook, Gmail) have a dedicated button for reporting phishing.
By doing this, you help protect other users.and the system will automatically block similar messages in the future.
Step 5: Report the incident to the appropriate place
If the message concerns your work, company account or company systems – report the matter to the IT department or your supervisor.
Additionally you can:
• report the incident to CERT Poland,
• send a message to CSIRT NASK (with an appropriate attachment),
• inform the Police if the content of the email contains threats or a ransom demand.
Step 6: Change Passwords (If You Clicked Anything)
If you inadvertently clicked on a link, downloaded a file or provided data – act immediately:
• disconnect your computer from the internet,
• change passwords to all important accounts (e-mail, banking, company systems),
• scan your device with antivirus software.
The faster you react, the greater the chance you have to avoid serious consequences.
Step 7: Remind your team or family about the rules
If you work in a team, manage a company or simply care for your loved ones, it's worth remembering how recognize phishing and what to do if you suspect fraud. Even the best security systems cannot replace conscious user.
We can help you with that
At ProsteIT, we support companies and users in analyzing phishing incidents, configuring security filters, and providing cyberthreat training. If you want to secure your IT environment or analyze a suspicious message – you can count on us.

How to protect yourself against phishing?
Protecting yourself against phishing isn't just about installing antivirus software or clicking less - it's a holistic approach to digital security, where habits, awareness and common sense are as important as technology.
The most common victims of phishing are not "non-technical" people - but those who they are sure that nothing will happen to them, because "they don't click on stupid things."
Meanwhile, fraudsters today invest in psychology more than malware – their messages can look perfect, and emotional manipulation is their greatest weapon.
So how can you protect yourself effectively?
Start with the simplest steps.
If you use e-mail, online banking or social networking sites, set two-factor authentication (2FA)This is a simple change that blocks most account takeover attempts, even if someone knows your password.
Remember to use a different password for each account – and if you can't remember them, use password manager (e.g. Bitwarden, 1Password or KeePass).
But technical security is only one side of the coin. The other is awareness and caution in everyday communication.
When you receive an email with an invoice, a request for a transfer, a password change, or a link to a "package you didn't order"—take your time. Stop. Read it again.
If something seems even a little strange – most often something is actually wrong.
Instead of taking risks, call the sender, visit the website yourself, and consult with someone you trust.
In the case of companies, it is worth going a step further: configure anti-phishing filters, add SPF/DKIM/DMARC to your email domain, set warnings for messages from outside the organization, and even prepare a short training session for the team. Sometimes a single meeting is enough to avoid losses amounting to thousands of zlotys.
What's important: phishing it's never a matter of "if", but "when"Every business—from a sole proprietorship to an accounting firm or online store—will sooner or later encounter a fraud attempt. So it's not about living in fear. It's about being prepared.
And that's exactly what we can help you with.
From security configuration, to message analysis, to team training, we know how to simplify cybersecurity, even if no one in your company has dealt with it before.
No complicated jargon and no pressure for expensive solutions – simply effective and understandable.

Phishing in companies – a real threat to business
Phishing isn't just a problem for individual users. For many companies—from accounting firms to transportation and manufacturing companies—it's one of the most real business threatsthat they face every day. Why? Because It is easiest to attack a person – not a system.
Unlike technical attacks, phishing attacks in companies often don't require any security breaches. All it takes is one careless click, and login details for accounting systems, CRM, company email, or servers end up in the wrong hands.
In practice, we encounter recurring scenarios:
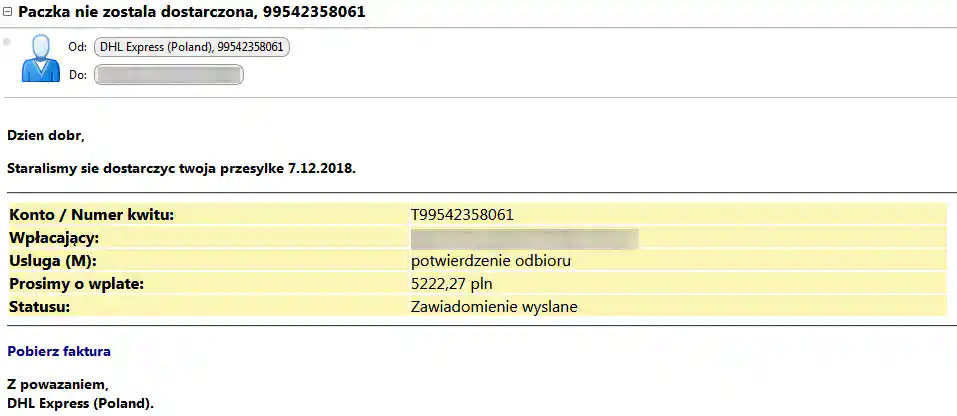
• Fake invoice from a "new contractor" with a suspicious attachment,
• E-mail from the "boss" asking for a quick transfer,
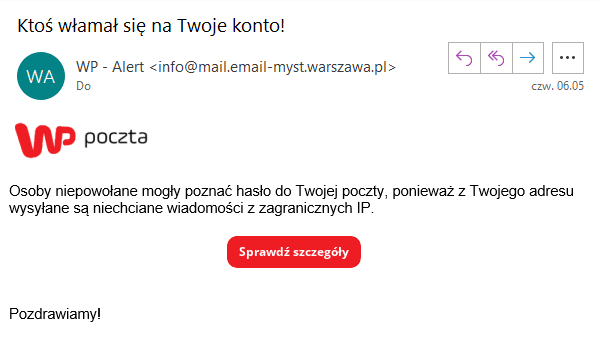
• A message from the "IT department" with a link to change your password,
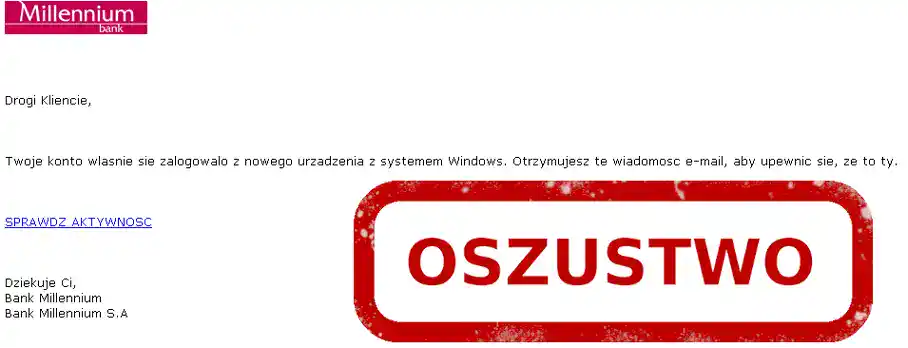
• Warning from the "bank" about the suspension of the company account.
Each of these email scams appears legitimate, to the point where an unwitting employee can make a transfer, click a malicious link, or provide access data. This can lead to financial losses, GDPR violations, or the paralysis of an entire team.
It is worth remembering that IT systems can be rebuilt, but reputation is much more difficult.
That's why more and more companies are considering phishing education as part of their security strategy. It's not about hours of training, but about awareness of everyday threats: how to recognize phishing, when to report a suspicious message, how not to give in to time pressure.
If you don't have an internal IT department or simply don't want to risk your problem being ignored, you can count on our support.
We help companies:
• configure anti-phishing protection,
• train employees (briefly, specifically, with examples),
• analyze suspicious messages,
• react to incidentsbefore they become a crisis.
Phishing can't always be stopped – but you can be prepared for it.
And this is exactly what we help our clients with – effectively, clearly and without stress.
Frequently asked questions
How do I know if the message is phishing?
Can I get infected just by opening an email?
I clicked on a suspicious link – what now?
Is every threatening message a scam?
Does antivirus software detect phishing?
Where to report a phishing attempt?
Summary + How We Can Help You
Phishing is one of those threats that seems obvious at first glance—until a message arrives that looks surprisingly credible. In this article, I've shown you a real-world example, a thorough analysis of the scam, and specific tips. how to recognize phishing and how to react when such a message arrives in your inbox.
Whether you are a private person or run a business – it is worth taking action in advance, before clicking on a suspicious link brings real consequences.
For small and medium-sized businesses, the consequences of a phishing attack can be particularly devastating: data loss, downtime, legal fees, or GDPR violations. And it often all starts with a single careless click.
That's why we offer specific, accessible IT support for companies from Warsaw, Pruszków, Ożarów Mazowiecki and the entire Masovia region – even remotely, if you operate in another part of Poland. You don't need to be an expert in cybersecurity – that's what we're for.
We can help you with, among other things:
• analysis of suspicious phishing messages,
• configuration of security filters on company mailboxes,
• implementing two-factor login (2FA),
• employee education and preparation of internal procedures,
• quick response to security incidents in the company.
If you found this article helpful – share it with your loved ones or colleaguesThe more people know, how phishing works, the harder it is for fraudsters to achieve their goal.
Do you have questions? Do you have doubts? Or maybe you just received a strange email and don't know what to do with it?
Contact us – via form, phone, email, WhatsApp or Microsoft Teams.
We'll take care of it. No stress, no fuss, just effective.