Imagine turning on your company computer one morning to discover that all your files—offers, contracts, customer data—are inaccessible. A hard drive has crashed, an employee has accidentally deleted a folder, or an outsider has encrypted your resources in a ransomware attack. This isn't a movie script—situations like this happen every day, even in small and medium-sized businesses.
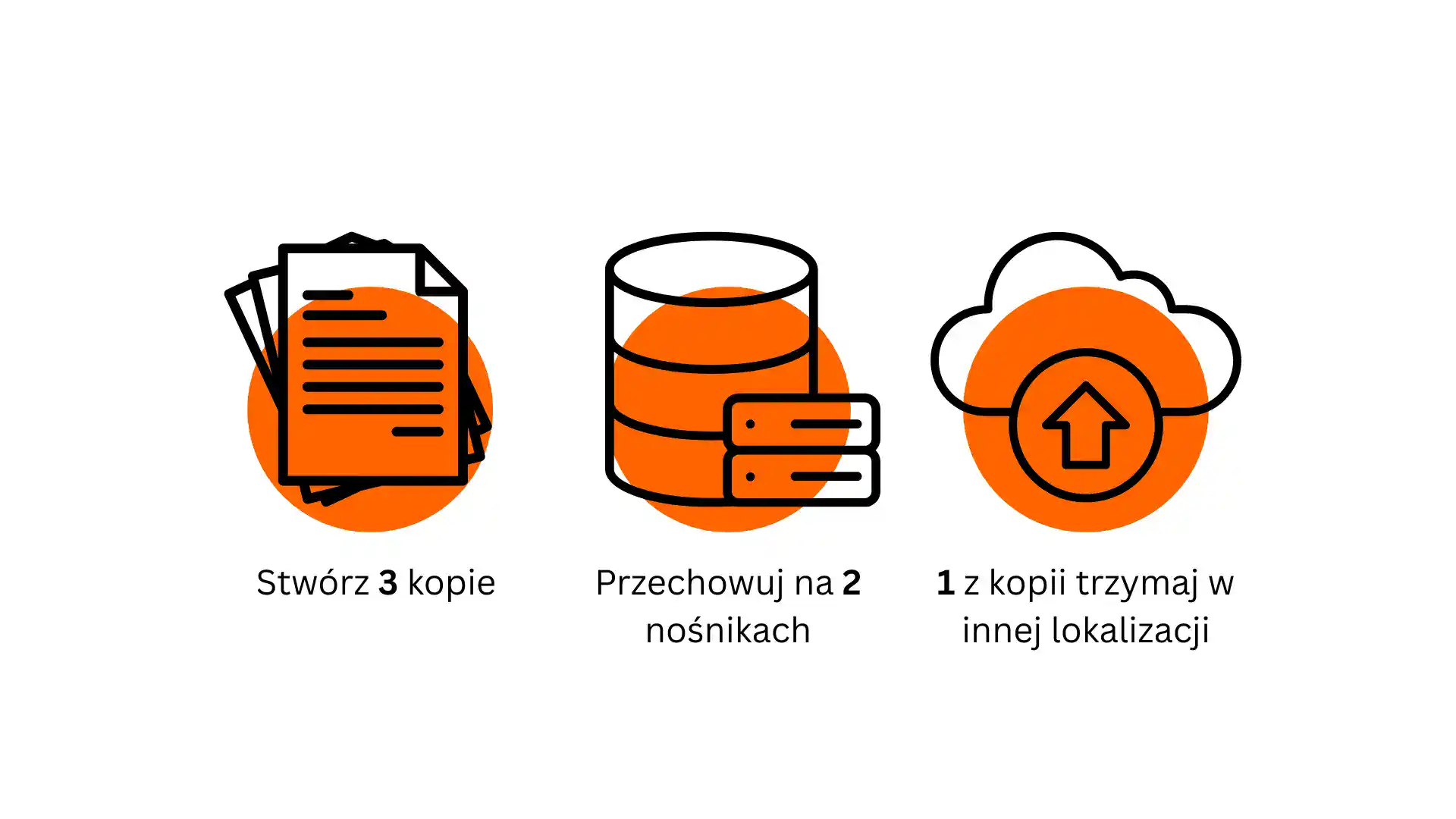
That's why it was created 3-2-1 backup ruleThis simple approach allows you to maintain business continuity even if your main systems fail. In short, it means three copies of your data, on two different media, with one copy stored off-site. This reduces the risk of complete file loss to virtually zero.
In this article I will explain to you how it works 3-2-1 backup, I'll show you how to implement it in a small business step by step and what mistakes to avoid. You'll also learn about modern alternatives to this method, and at the end, you'll read a short case study demonstrating its effectiveness in practice.
If you're looking for a simple way to protect your data and sleep soundly, you've come to the right place.

The 3-2-1 backup rule in a nutshell
Backup 3-2-1 This is one of the simplest and most effective methods of securing data. Its strength lies in its simplicity:
• 3 copies of data – In addition to the original, there should be two additional copies. This way, even if one fails, you still have another source of file recovery.
• 2 different media For example, one copy on a local drive and another on an external NAS server or in the cloud. This minimizes the risk of failure of one type of device.
• 1 copy outside the company's office – a key element that protects against fire, flooding, and theft. Even if the entire office goes down, a copy in another location will allow you to quickly return to work.
A real-life example: a company stores data on employee computers, makes additional copies on an office server, and uploads a third version to the cloud. This is a classic 3-2-1 implementation.
RPO and RTO explained simply
Two abbreviations often appear in the context of backup: Ombudsman and RTOIt's worth knowing some basic things about them:
• Ombudsman (Recovery Point Objective) determines how much data you can lose since the last backup – for example, if the backup is performed once a day, you can lose up to 24 hours of work.
• RTO (Recovery Time Objective) tells you how long it will take to restore data and return systems to normal operation.
At this stage it is enough to understand that 3-2-1 backup significantly improves both indicators – reduces data loss and shortens recovery time.
Why It Works: The Most Common Threats 3-2-1 Protects Against
Ransomware and asset encryption
Ransomware attacks involve encrypting files and demanding a ransom to unlock them. Unfortunately, paying criminals doesn't guarantee data recovery. In practice, the only effective protection is to have copies that the ransomware won't affect—that is, offsite backup (outside the local network) or immutable copies. This allows you to restore your resources risk-free and at no additional cost.
Equipment failure
Every hard drive or server eventually fails. Sometimes SMART errors signal this, but in many cases, the problem occurs suddenly. If all data is stored on a single medium, its loss is only a matter of time. 3-2-1 means that even a failure of the main server does not stop the work - just reach for one of the additional copies.
Human error
Even the most organized team makes mistakes—accidentally deleting a folder, overwriting an important document, formatting the wrong drive. Backups protect against the consequences of such situations. Multiple file versions allow you to revert to a pre-error state and continue working without loss.
Theft, fire and other random events
Companies are increasingly realizing that threats don't have to be digital. Equipment theft, fire, or office flooding can destroy both data and local copies. In such cases, having a copy stored in a different location becomes crucial—following the principle 3-2-1.
Thanks to this approach, backup is no longer a “just in case” option, but a real safeguard against situations that can stop your business for many days.

How to implement 3-2-1 step by step in your small business
Implementation of the principle 3-2-1 backup doesn't have to be difficult or expensive. The key is a systematic, step-by-step approach. This way, even a small company can have professional system data protection, without having to invest in complex corporate solutions.
Data inventory and priorities
To start with, you need to answer some simple questions:
• What data is critical to the company's operations? (e.g., customer database, accounting documents, projects).
• Where is it currently stored? (employee computers, file server, cloud email).
• Who should be responsible for creating and monitoring copies?
Thanks to this inventory, it is easy to determine what really needs to be protected and what data requires more frequent copies.
Selection of media and locations
The 3-2-1 rule requires diversity – so simply copying files to the same server isn't enough. Practical combinations include:
• local server or NAS – quick access to files when needed,
• cloud – a second copy outside the office, resistant to local failures,
• offline medium (e.g. external drive rotated once a month) – additional protection against ransomware.
This arrangement meets all the elements of the 3-2-1 rule and does not require huge expenditures.
Schedule, Retention, and Policies
The copy itself is not everything – you also need to plan the frequency and method of its execution:
• schedule – e.g. daily backup for documents and weekly backup for archives,
• retention – specify how long you keep old versions of files (e.g. 30 days, 6 months, a year),
• policy – simple rules written in the document: who is responsible, how to report errors, what to do in case of a failure.
This means that copies are not made “from time to time”, but in a predictable manner.
Playback Testing and Documentation
The biggest mistake companies make is lack of testing – backups exist, but no one has verified whether they can be restored. Therefore, it's worth running a recovery test at least quarterly, for example, restoring a few files or the entire environment to a backup machine. This is the best way to ensure that the backup is truly working.
At this stage, simple documentation is also useful – a list of steps and responsible persons that can be taken out of the drawer in a crisis situation.
This approach provides even a small business with a backup system that is predictable, fault-tolerant, and easy to manage. If you'd like, we can assist you with the entire process—from data analysis, through media and software selection, to backup testing and monitoring.

Variants and modern extensions of the 3-2-1 rule
Although the rule 3-2-1 backup remains the foundation of data protection, and in recent years, extensions have emerged to address new threats, particularly cyberattacks and the growing role of the cloud in business.
3-2-1-1-0 and unchangeable backup
There is more and more talk about the model 3-2-1-1-0. It adds two elements:
• 1 additional copy offline or immutability – that is, one that cannot be changed or deleted (e.g., editing lock in backup systems). This is the best protection against ransomware.
• 0 errors after integrity verification – means that each copy is automatically checked and confirmed as correct.
Thanks to this, companies can be sure that their data is not only archived, but also inviolable.
Microsoft 365, Teams and cloud email
Many entrepreneurs assume that using cloud services like Microsoft 365 automatically solves the backup problem. Unfortunately, this is only partially true – yes, data is protected against Microsoft server failures, but not against user errors, ransomware, or accidental deletion of messages. cloud copies also require additional backup, e.g. in a separate Veeam environment.
Air-gapped and disconnected copies
In the era of ransomware attacks, solutions are gaining popularity air-gapped – that is, physically disconnected from the network. This could be a rotating external drive or magnetic tape stored off-site. Such media is not accessible online, so no attacker can access it.
Encryption and key protection
It is also becoming increasingly important data encryptionBackups should be protected both in transit and at rest. It's important to ensure that encryption keys are stored separately and securely – this provides an additional layer of protection that prevents unauthorized access to backups.
Modern enhancements don't change the foundation – the 3-2-1 rule is still the starting point. However, adding elements like immutability and offline copies makes backups resistant to even the most advanced attacks.
Tools, automation and reporting
Even the best backup plan won't work in practice if the process is too complex or relies on employee memory. That's why it's so important to use the right tools—those that allow automate the creation of backups, monitor their status and receive reports on possible problems.
What's Really Important in Backup Software
When choosing a backup system, there are a few key features to consider:
• Task automation – copies should be made automatically, according to a set schedule, without the need for manual intervention.
• File versioning – the ability to store multiple versions of the same document to restore the state before an error or infection.
• Verification of copy accuracy – each copy should be checked for integrity to avoid files becoming unusable at a critical moment.
• Alerts and reports – the system should automatically inform about the success or failure of the backup, and also create clear reports for the person responsible for data security.
Thanks to such features, backup ceases to be a "black box" and becomes a transparent process that provides assurance that the company is secured.
Technology partnerships matter
There are many solutions available on the market, but not all are equally effective or tailored to the real needs of small and medium-sized businesses. Therefore, it's worth using proven systems. At prostoIT, we work with Veeam, one of the leaders in data backup and recovery. This allows us to select a solution that perfectly suits your business – from simple email and file backups to advanced scenarios with virtual machine and cloud backup.
Automation and reporting ensure backups run in the background, giving you clear visibility into their status. This saves time, increases security, and provides peace of mind that's hard to overestimate.
Case study: rapid implementation of 3-2-1 in a service company
Starting point
A small service company employing around 25 people stored all its data on a local file server. Once a day, a backup was made to an external USB drive connected to the same server. At first glance, the backup seemed to be working; in reality, it was a system vulnerable to failure, theft, or ransomware attacks.
Implementation
During the security audit, we proposed a simple plan that followed the principle 3-2-1:
• current copies made automatically to the NAS server,
• an additional copy sent to the cloud daily,
• once a month, rotated offline media stored outside the office.
We supplemented everything with email reports and data recovery tests so that the team could be sure that the backup would actually work if necessary.
Effect
Following implementation, the company gained confidence that even in the event of a server failure or ransomware attack, key files would be available within hours. Importantly, the entire process was accomplished without excessive costs and with minimal employee involvement.
This short implementation shows that 3-2-1 rule is not a theoretical concept from IT textbooks, but a practical tool that actually protects the business and ensures business continuity.
Frequently asked questions
Is cloud backup enough as the only copy of data?
How much does it cost to implement 3-2-1 backup in a small business?
How often should you make backups?
Do you really need to back up cloud services like Microsoft 365?
Principle 3-2-1 backup This is a simple yet extremely effective method of data protection. It allows your company to operate without worrying about hardware failures, employee errors, or cyberattacks – you can always be sure that key files are available and can be quickly restored.
Implementation doesn't have to be complicated or expensive. A well-chosen tool, a clear plan, and regular testing are all that's needed. By collaborating with technology partners like Veeam, we can provide you with solutions tailored to the scale and needs of your company - from simple copies of mail and documents to advanced scenarios covering the entire IT environment.
If you want to ensure your company's backups truly work and won't fail at a critical moment, contact us. We'll be happy to help you plan, implement, and monitor your backups so you can focus on growing your business.