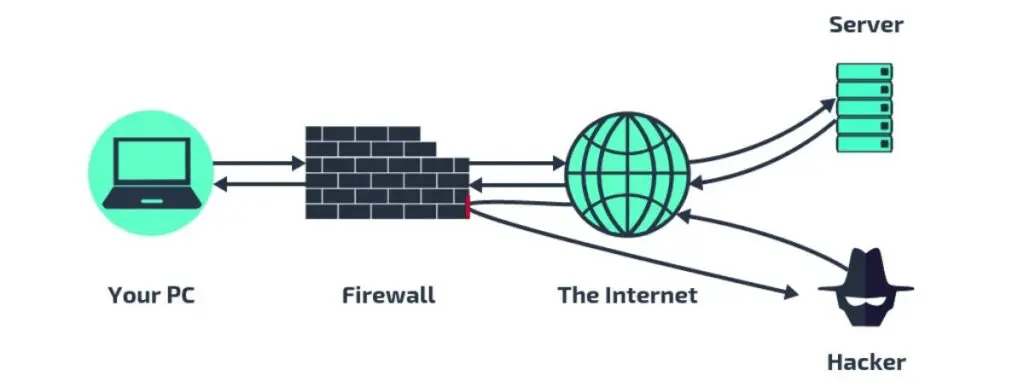
Imagine your computer is your office. Every day, someone knocks on his door—emails, websites, apps, updates. Some of these "guests" are welcome, but others try to get in uninvited, sometimes even under false pretenses. And that's where it comes into play. firewall – a silent security guard who decides who can enter and who is stopped at the threshold.
Although its name sounds technical, firewall is one of the most human technologies in the IT world, it's guided by the principles of trust, caution, and common sense. Without it, even the best antivirus or backup software won't be enough to ensure the security of corporate data.
In this article, I will show you what a firewall really is, how it works in simple words, what types there are, and why every company needs one today – regardless of whether you have a single computer or an entire office network.

Firewall in a nutshell: what exactly is it?
Word "firewall" It sounds ominous, a bit like a term from a hacker movie. Literally translated, it means "firewall"—a barrier that stops fire before it spreads. And that's the best metaphor for its role in the world of computers.
In simple terms A firewall is a fundamental element of any network's security.It protects devices from unauthorized access, minimizes the risk of cyberattacks, and allows you to maintain control over what's happening in your company's infrastructure.
In practice it works like this security guard at the entrance to the officeIt checks who's trying to access (i.e., connect to your device), where they're coming from, and whether they have good intentions. If something looks suspicious, it won't let them in. If everything looks okay, it lets them through.
The firewall determines which data can pass through your network's "doors" and which is blocked. It analyzes every communication attempt and compares it to established security policies, called rulesThis allows it to filter network traffic – both incoming and outgoing.
What is important, firewall not only protects, but also learns behavior patterns on the network. In newer solutions (such as so-called next-generation firewalls), it can recognize specific applications, block access to dangerous websites, and even analyze whether anyone in the company is trying to send sensitive data outside the organization.
For the end user, the firewall usually works in the background – without the need for constant maintenance. In Windows systems, its basic version is built-in and works automatically. In companies, however, it is often used professional network devices, which filter all traffic passing through the Internet before it reaches employee computers.

How a firewall works
Although a firewall may seem complicated at first glance, its purpose is very specific: controls network traffic – i.e. all data that enters and leaves your computer or company network.
Every device connected to the internet is constantly "talking" to others: downloading pages, sending messages, updating software, and synchronizing files. Each of these operations involves the exchange of thousands of small pieces of information, called data packetsThe firewall analyzes these packets, checking their source, destination, and content, and then makes a decision whether to allow or block them.
Address and port level control
The basic way a firewall works is call filtering by IP addresses and ports.
• IP address identifies a device on the network (e.g. computer, server or telephone).
• Port instead, it indicates the specific service or application from which the data comes (e.g. web browser, email, remote desktop).
The firewall has a defined set of rules that tell it which combinations of addresses and ports are allowed and which are not. For example:
• connections from trusted addresses can be passed without restrictions,
• communication attempts from unknown or blocked countries are rejected,
• access to the company server is only possible from specific addresses.
It is this level of control that allows you to stop unwanted traffic before it even reaches your computer.
Packet analysis – the heart of the firewall
Before being passed on, each data packet is checked by the so-called packet inspection engine (eng. packet inspection engine).
The simplest firewalls operate based on static rules – they simply check whether a given package meets the established criteria. More advanced solutions use state inspection (stateful inspection), meaning they track entire connections in real time. They know that if computer A initiates a conversation with server B, the response from B is part of the same, secure dialogue. This allows the firewall to distinguish trusted from suspicious traffic.
The so-called go even further. Next Generation Firewalls (NGFW)In addition to classic packet analysis, they recognize applications (e.g., Teams, Dropbox, YouTube), users, and specific data types. They can also stop malicious traffic hidden in regular network connections, detect intrusion attempts, and filter web content by category.
Security policies and rules
The heart of the firewall is security policy – sets of rules defining what traffic is allowed.
The administrator can define rules such as:
• allow outgoing traffic from the office network to the Internet,
• block traffic coming from outside the country,
• allow access to the accounting server only from the VPN network,
• log all connection attempts from blocked addresses.
Rules are checked in a specific order—from top to bottom—until the firewall finds a match. If none match, the so-called default rule (most common: block). This prevents accidental, unauthorized traffic from getting through.
Logging and reporting
Each event – both blocked and allowed connections – can be recorded in event log (logs). This is not only proof that the firewall is working, but also an invaluable source of information about potential incidents. Modern solutions allow for real-time analysis of reports, allowing for quick response to unusual activity, such as mass login attempts or a sudden increase in traffic from a single country.
Working in the background, but with real impact
Even though most users don't even notice its presence, the firewall is key security checkpointIt is the controller who decides whether the connection will be accepted or rejected, and its decisions directly impact data protection, system stability, and service availability.
From a business perspective, it is worth remembering that Improper firewall configuration can be as dangerous as its absenceToo loose rules open the door to attackers, while too restrictive ones can hinder the work of users and applications. Therefore, it's best to entrust configuration to specialists who can balance security with ease of use.
Types of firewalls: from home to corporate
Firewalls vary in their operation and scope of protection, but their goal is the same: to protect networks from unwanted traffic. In practice, there are four types that are of real importance in everyday use, from home computers to corporate networks.
1. Software firewalls
These are firewalls that run directly on your computer or server. Their purpose is to application controlwho are trying to use the Internet, and blocking unauthorized connections.
The most famous example is Windows Defender Firewall, which automatically protects the system from malicious incoming and outgoing traffic. A popular solution for more aware users is also GlassWire, which, in addition to protection, offers clear visualizations of network traffic.
The advantage of software firewalls is their simplicity – they require no additional hardware and operate immediately after system installation. They are effective in homes and small offices, where each computer operates independently. Their disadvantage, however, is their limited range – they protect only the device on which they are installed.
2. Firewalls in routers
Most modern routers have a built-in firewall. This works across the entire local network, separating it from the Internet and filtering incoming calls.
This allows every device on the network—computer, phone, printer, or IP camera—to benefit from the same basic protection. This solution is very effective for homes and micro-businesses where extensive administration is not necessary.
All you need is proper configuration: changing default passwords, enabling automatic updates, and—if your device allows it—activating content filtering or an SPI firewall. A well-configured router can filter out most simple threats.
3. Hardware and network firewalls
In companies where many devices and users operate, the so-called hardware firewalls – Special devices placed between the corporate network and the internet. This is the central point of protection through which all traffic passes.
Such solutions, offered by, among others, FortiGate, Ubiquiti, Mikrotik, Cisco Whether Sophos, provide:
• control of access to the Internet and applications,
• creating a VPN network for remote work,
• detection of intrusion attempts (IDS/IPS),
• filtering dangerous sites and content.
A hardware firewall protects not only individual computers but also the entire infrastructure—from servers to network devices. It is stable, operates independently of user systems, and ensures a high level of security, especially in environments where customer data is processed or online accounting is conducted.
4. Cloud Firewalls
With the popularization of remote work and tools such as Microsoft 365 Whether Google Workspace, more and more companies are reaching for cloud firewallsThey work not on the device or in the office, but on the Internet, between the user and the cloud resources.
This allows them to protect employees regardless of their connection location—office, home, or travel. They enable centralized management of security policies and traffic filtering without the need for hardware maintenance.
This solution is particularly useful in distributed companies where users work from different locations and data resides in the cloud. A cloud firewall provides consistent protection, regardless of where users log in.
Selecting a solution
The choice of firewall type depends on the scale and method of operation:
• a private person or freelancer needs a system firewall enabled and a well-configured router,
• a small or medium-sized business should invest in a network device or cloud firewall that centrally protects data and users.
Regardless of the solution chosen, the most important thing is a conscious approach to security – regular updates, well-thought-out rules and control over who has access to the network.
As part of our services, we help you select and configure firewalls tailored to your specific needs – from simple home firewalls to enterprise-class solutions from FortiGate or Ubiquiti. This ensures your network remains protected without slowing down user experience.
Popular Solutions and Where They Make Sense
The firewall market is vast—from simple system firewalls to complex enterprise solutions. They vary in capabilities, but each has its place and application. Here are the most common types and the situations in which they are worth using.
Windows Defender Firewall
For whom: individual users and small offices
This is a firewall that every computer with the system has WindowsIt works automatically and provides basic protection – it blocks unauthorized connections, allows you to create simple rules, and protects against external access.
It makes sense, if you use the computer alone or in a small office without an extensive network.
GlassWire
For whom: aware users, freelancers, small teams
This firewall With a clear interface that visualizes network traffic and shows which applications are connecting to the internet, it makes it easier to detect suspicious connections and provides more control than a built-in firewall.
It makes sense, if you want to know what's really "going on" in your network, but without having to use professional administration tools.
Firewalls in routers
For whom: homes, micro-businesses, small offices
Every modern Wi-Fi router has a built-in firewall that filters connections between the local network and the internet. This is a simple yet effective first line of defense.
It makes sense, if you want to protect your entire network (e.g. computers, printers, cameras) without investing in additional hardware.
FortiGate, Mikrotik, Ubiquiti, Sophos (corporate solutions)
For whom: companies with more than a few employees or servers
These are hardware firewalls that protect the entire network (Mikrotik performs better as a router). They offer traffic filtering, secure VPN connections, application and user control, and detailed security reports.
They make sense, if your company stores customer data, uses accounting systems, or operates remotely. They provide real control and assurance that the network is being monitored.

Firewall, antivirus and EDR – what is responsible for what?
In the world of cybersecurity, there's no single tool that protects against everything. Each element has its own role, and only together do they create coherent, effective protection. It's important to understand What is the difference between firewall, antivirus and EDR?, and why none of them replaces the others.
Firewall – the guard at the entrance
Firewall controls network traffic – decides which connections can be established and which should be blocked. Protects devices and networks. at the communication level – before the threat reaches the system. It doesn't analyze files or remove viruses, but it prevents them from entering from the outside.
This is the first line of defense – it stops intrusion attempts, blocks unauthorized connections, and protects servers and users from access from unknown sources.
Antivirus – system doctor
Antivirus deals with what is already on your computerScans files, applications, and memory for malware – viruses, Trojans, ransomware, and keyloggers.
It reacts when something has managed to penetrate the network or has been launched by a user. It works reactively, but it's necessary because no firewall can stop, for example, a virus from a flash drive or a malicious file opened locally.
EDR – Analyst and Detective
EDR (Endpoint Detection and Response) is a modern tool for monitoring system behaviorIt not only detects threats but also analyzes their source, mode of operation, and effects. It can recognize unusual activity—for example, sudden file encryption, attempted system modification, or communication with a malicious server—and respond automatically, isolating the device from the network.
In large companies, EDR is now a standard, while in smaller companies it is increasingly becoming an extension of traditional antivirus.
Only the cooperation of these tools creates a complete protection system – from prevention, through response, to threat analysis.

What does a firewall actually offer to SMEs?
For many business owners IT security sounds like something far away – until the problem actually occurs. Meanwhile, a well-configured firewall can stop many threats before they can cause damageHere are some examples from everyday situations where his role proves crucial.
1. Attacks from unknown IP addresses
Anna runs an accounting firm. Every few days, she notices someone trying to log in to the server containing client data. The firewall detects these attempts and automatically blocks connections from addresses outside Poland. The result? Attacks from foreign bots end before they can do anything.
Advantage: data protection and owner peace of mind without the need for constant monitoring.
2. An employee opens a suspicious attachment
Mr. Krzysztof from a trading company receives an email with an invoice from a "new customer." The file turns out to be infected. The firewall blocks the connection to the server from which the malware attempted to download further instructions. The antivirus system removes the threat before anything is encrypted.
Advantage: avoiding company downtime and loss of customer data.
3. Securing remote work
Part of the service company's team is working from home. The company's firewall forces connections through a secure VPN, so data isn't transmitted over open channels. Employees can use applications and servers as if they were in the office—while the company maintains full control over who has access.
Advantage: secure remote work and reduced risk of data leakage.
4. Protection of company devices
In a small construction company, laptops, a printer, cameras and an alarm system are connected to the same network.
A firewall separates office devices from the rest of the infrastructure and prevents malware from spreading from one piece of equipment.
Advantage: greater security of the entire network – even with simple IoT devices.
The firewall is not visible on a daily basis, but runs in the background when something undesirable happensThanks to this, many security incidents never make it beyond the testing phase.

Basic Firewall Configuration: Headache-Free Best Practices
A firewall alone doesn't guarantee security. What really determines its effectiveness is configuration – the way network traffic rules and regulations are defined. You don't need to be a network administrator to understand the basics. All you need are a few best practices that can be implemented in any company, regardless of scale.
1. The principle of limited trust – allow only what is necessary
By default, most devices and applications want to access the internet, but not all need it.
The safest approach is blocking everything that is not necessary and gradually adding exceptions.
If a given connection is not necessary for work, it is better to turn it off.
In practice, this means:
• blocking unused ports (e.g. 21 – FTP, if you do not use it in the company),
• limiting access to the router or server administration only from the internal network,
• using whitelists instead of blocklists.
This is a simple way to close potential loopholes for attackers.
2. Regular software and firmware updates
Surprisingly often companies invest in good equipment, but they haven't updated it for yearsMeanwhile, new software versions fix bugs and vulnerabilities that could be exploited by cybercriminals.
Updates apply not only to Windows, but also to:
• routers,
• hardware firewalls,
• security software (antivirus, EDR).
It is best to set automatic notifications or request updates. IT company – they take a few minutes and can prevent serious problems.
3. Backing up your configuration
Many people forget about this until they need to restore settings after a failure. It's always good to have a copy of the firewall configuration – especially in companies where the devices are more complex.
In the event of a hardware error, reset, or replacement, you can restore your system to its previous state in minutes, instead of having to configure everything from scratch. It's best to perform this backup after any major rule changes or software updates.
4. Separate corporate, guest, and loT networks
Modern routers and firewalls allow you to create separate logical networks (VLANs)This is one of the simplest, yet most effective security measures:
• company network – for employee computers and servers,
• guest network – for visitors and private devices,
• IoT network – for cameras, printers, alarm systems.
This means that even if one device is infected, it will not threaten the rest of the infrastructure.
5. Enable VPN instead of opening ports
A common mistake in companies is to expose services (e.g., remote desktop, accounting system) directly to the internet. Instead, it's worth using VPN (Virtual Private Network) – a secure tunnel that connects the user to the corporate network.
A VPN encrypts the connection and requires authentication, making it impossible for outsiders to see what services are running within the company. For many small businesses, a built-in VPN in a firewall or router is sufficient—this feature makes a real difference.
6. Monitor logs and respond to warnings
Most firewalls record detailed event logs (logs)It's a good idea to review them at least once a week or set up automatic alerts – for example, email notifications when unusual activity or multiple failed login attempts occur.
It's not about constantly monitoring traffic, but about being aware of what's happening on your network. Detecting a problem early can help prevent more serious consequences.
7. Review the rules periodically
Over time, the way of working in every company changes – new applications, people, and services appear.
That's why it's worth it once every few months review firewall configuration and remove unused or obsolete rules.
Old exceptions, open ports, or unnecessary VPN access are common sources of threats that are easy to miss.
A clean, up-to-date configuration not only ensures greater security, but also better network performance.
8. Cooperation with an IT company
Not every company has its own network administrator. In such a situation, the best solution is constant IT support for companies. External IT support (like us ;)) maybe:
• monitor security status,
• update software,
• restore configurations after a failure,
• respond to firewall alerts.
This means the owner does not have to deal with technical details, and the network remains secure and stable.
A well-configured firewall doesn't require daily attention. It operates quietly, effectively, and without disrupting users. A few well-thought-out rules are all it takes to provide your network with real protection—without unnecessary complexity.
We help companies implement and configure firewalls that balance security and convenience. This way, technology doesn't get in the way—it just works.
A Firewall Isn't Everything - How to Build Complete Security
A firewall is an important element of security, but it alone won't ensure the complete security of a company's network. Modern cyber threats bypass individual security measures, so effective protection relies on several complementary layers.
Each of them has a different purpose and together they create a coherent security structure.
1. Updates and patches
Without regular updates, even the best firewall won't help. Vulnerabilities in operating systems, browsers, and routers are the most common entry points for attackers.
2. Antivirus and EDR
A firewall stops dangerous network traffic but doesn't remove malicious files already on the system. Antivirus or EDR analyzes device behavior and responds if something looks suspicious.
3. Backups
Even if all security measures fail, backup allows you to recover data after a ransomware attack or failure.
This is the last line of defense, often the only one, that saves the company from downtime.
4. VPN and Access Control
Remote network access should only be via encrypted VPN connections and using strong passwords or multi-factor authentication (MFA). Open ports are a prime candidate for hacking.
5. User education
Many attacks can be avoided with employee awareness. Users are most likely to click on infected links or enter login details into fraudulent forms. Simple training can significantly reduce the risk.
Firewall is the foundation, but only the combination of network, system and user protection creates a real security shield.
Frequently asked questions
No. A firewall is essential, but effective security also requires system updates, antivirus, backups, and appropriate access policies. Only a combination of these elements provides real protection.
For homes and small offices, such a firewall is often sufficient. For companies that store customer data or have multiple workstations, it's worth investing in a professional hardware or cloud firewall.
The simplest solution is to try blocking the selected application or connection and see if the rule works. Companies recommend periodic security tests and log reviews to ensure the firewall is responding to suspicious traffic.
For home users, yes, as long as the system and router are up-to-date. For businesses, it's better to choose a solution with reporting, user control, and remote management capabilities, which provides greater visibility and security.
No, if it's properly configured and sized for the traffic volume. Speed issues mainly occur with cheap devices or excessively active filters.
Your device will become visible online and vulnerable to scanning and hacking attempts. Even a few minutes without a firewall can be enough for automated bots to find a vulnerability and exploit it.
A firewall is one of those tools that operates silently but is crucial to the security of any company. It protects the network from unauthorized access, filters connections, and stops many threats before they reach employee computers.
However, it does not replace other security measures – it is first line of defense, which should be supplemented with updates, antivirus, backups, and good user practices. Combined, they create a protection system that not only responds to problems but, above all, prevents them.
A firewall doesn't have to be complicated - it just has to be well-fitting, properly configured and regularly maintainedThese are simple steps that truly increase your company's security and allow you to focus on what matters most – your daily work.





